0x00 前言
该系列主要用于记录密码学实验过程中遇到的题目及相关分析方法.
0x01 Cryptopals部分题目
该部分题目参考Cryptopals系列博客Set1部分,链接如下:
Cryptopals-Set1
0x02 Many Time Pad
题目链接
Coursera-Cryptography-Week1-PA
题目描述
Let us see what goes wrong when a stream cipher key is used more than once. Below are eleven hex-encoded ciphertexts that are the result of encrypting eleven plaintexts with a stream cipher, all with the same stream cipher key. Your goal is to decrypt the last ciphertext, and submit the secret message within it as solution.
Hint: XOR the ciphertexts together, and consider what happens when a space is XORed with a character in [a-zA-Z].
1 | ciphertext #1: |
题目分析
该题目提供了十条使用同一密钥(有意义的英文语句)加密后的密文结果,要求根据所给的密文解密最终的target ciphertext.由提示,空格space与大写字母异或结果为小写字母,与小写字母异或结果为大写字母.而任意两个字母异或的结果不在字母范围内.又由于对于使用同一密钥进行异或加密的两对密文,其进行异或的结果等于对应明文进行异或的结果,如果结果的某个位置出现字母,则说明对应的两个明文位置的其中之一可能为空格.故对十一条密文进行两两异或,对于第一条密文,寻找可能为空格的位置,将该位置与其余密文对应位置的字符进行异或,设定阈值为6,当结果中有超过该阈值数量的字母时,可以确定该位置明文为空格,从而确定该位置的密钥.获取足够多密钥信息后,可以对目标密文进行解密.得到的结果有部分未还原部分,根据常识还原出最终明文,并根据结果还原密钥.代码如下:
1 | # -*- coding:utf-8 -*- |
0x03 Vigenere-like cipher
题目描述
Write a program that allows you to “crack” ciphertexts generated using a Vigenere-like cipher, where byte-wise XOR is used instead of addition modulo 26.
Specifically, the ciphertext
1 | F96DE8C227A259C87EE1DA2AED57C93FE5DA36ED4EC87EF2C63AAE5B9A7EFFD673BE4ACF7BE8923CAB1ECE7AF2DA3DA44FCF7AE29235A24C963FF0DF3CA3599A70E5DA36BF1ECE77F8DC34BE129A6CF4D126BF5B9A7CFEDF3EB850D37CF0C63AA2509A76FF9227A55B9A6FE3D720A850D97AB1DD35ED5FCE6BF0D138A84CC931B1F121B44ECE70F6C032BD56C33FF9D320ED5CDF7AFF9226BE5BDE3FF7DD21ED56CF71F5C036A94D963FF8D473A351CE3FE5DA3CB84DDB71F5C17FED51DC3FE8D732BF4D963FF3C727ED4AC87EF5DB27A451D47EFD9230BF47CA6BFEC12ABE4ADF72E29224A84CDF3FF5D720A459D47AF59232A35A9A7AE7D33FB85FCE7AF5923AA31EDB3FF7D33ABF52C33FF0D673A551D93FFCD33DA35BC831B1F43CBF1EDF67F0DF23A15B963FE5DA36ED68D378F4DC36BF5B9A7AFFD121B44ECE76FEDC73BE5DD27AFCD773BA5FC93FE5DA3CB859D26BB1C63CED5CDF3FE2D730B84CDF3FF7DD21ED5ADF7CF0D636BE1EDB79E5D721ED57CE3FE6D320ED57D469F4DC27A85A963FF3C727ED49DF3FFFDD24ED55D470E69E73AC50DE3FE5DA3ABE1EDF67F4C030A44DDF3FF5D73EA250C96BE3D327A84D963FE5DA32B91ED36BB1D132A31ED87AB1D021A255DF71B1C436BF479A7AF0C13AA14794 |
was generated by encrypting English-language text using the following C program:
1 |
|
(Of course, when encrypting I used a random key length and chose each byte of the key at random.) The plaintext contains upper- and lower-case letters, punctuation, and spaces, but no numbers.
Recovered the original plaintext.
题目分析
该题目的本质依然为密钥重复使用问题,只是披上了维吉尼亚的外衣.假设加密者使用的密钥为v-key,长度为length,密文为字符串ciphertext.则字符串cipherset0 = ciphertext[0+k*length]是被v-key[0]加密的内容,字符串cipherset1 = ciphertext[1+k*length]是被v-key1加密的内容,依次类推.按照这种方法,可以将密文ciphertext分割成length份,每份都被密钥v-key的同一位解密还原明文.对每个加密密钥v-key[index],穷举其所有可能的值,并与对应的cipherset里的内容进行异或解密,找到能将该cipherset所有内容解为可见字符的所有可能密钥值.通过上述方法首先枚举得到密钥长度length,然后改变判定为明文的条件(假设明文只有字母、数字、空格和符号),再进行穷举,最终还原出密钥并进行解密.
爆破密钥长度代码如下:
1 | # -*- coding:utf-8 |
输出结果如下图:
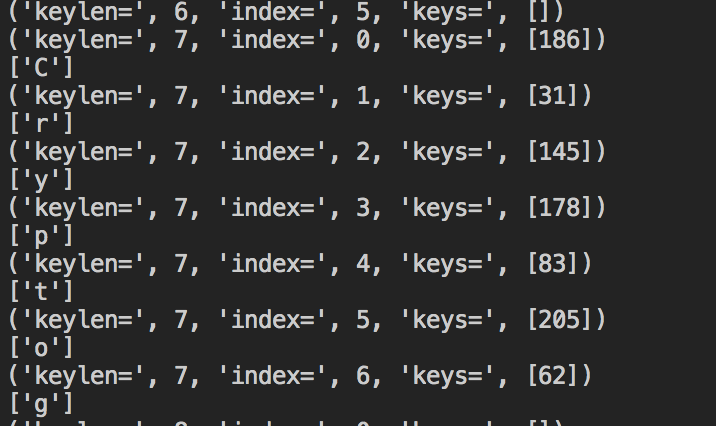
确定密钥长度为7后,直接进行穷举破解,得到最终密钥.
1 | vigenerekeys=[] |
最后使用得到的唯一密钥进行解密即可.
1 | plaintext = '' |
解密结果:
1 | Cryptography is the practice and study of techniques for, among other things, secure communication in the presence of attackers. Cryptography has been used for hundreds, if not thousands, of years, but traditional cryptosystems were designed and evaluated in a fairly ad hoc manner. For example, the Vigenere encryption scheme was thought to be secure for decades after it was invented, but we now know, and this exercise demonstrates, that it can be broken very easily. |
当然此破解过程也可以使用字母频率分析的方法来完成.
0x04 MTC3 Cracking SHA1-Hashed Passwords
题目链接
题目描述
The Secure Hash Algorithmus 1 has been standardized by the National Institute of Standards and Technology in 1995 and is besides MD5 the most commonly used hash algorithm in practice. An example for its usage is password-based authentification. In that case, the server does not store the user password in plain text but instead the SHA1 hash value of it. Once the user enters his password and after its received at the server, its hash value is computed and compared to the value stored on the server in order to verify its correctness.
A vulnerability of a surveillance system’s webserver leaked the SHA1 hash value of the password of the administrator account. The password’s hash value is
67ae1a64661ac8b4494666f58c4822408dd0a3e4
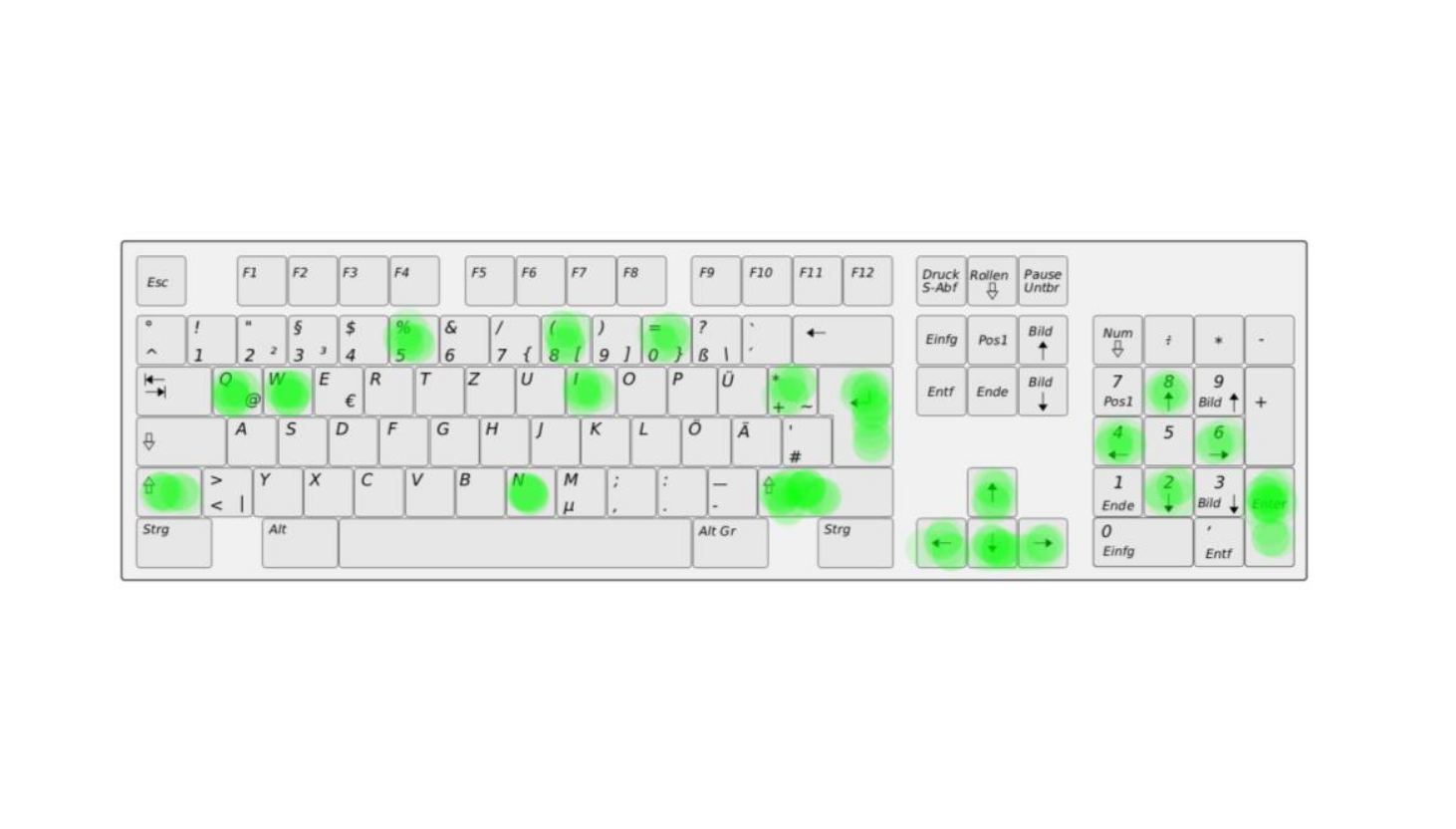
Furthermore, the keyboard of the login terminal shows clear signs of the entered password since after a successful login navigation in the software is only done via arrow keys. What is the password?
Remark: Note the German keyboard layout!
题目分析
该题目是一个简单的键盘还原问题,可以直接使用爆破的方法解决问题,注意需要考虑到时间限制.根据键盘上的按键分布,可以看出右边数字键只有2468,很有可能是当作上下左右的功能,对剩余按键按照每个键出现一次的原则进行暴力破解,可以得出最终键盘密码.脚本如下:
1 | # -*- coding:utf-8 -*- |
该程序破解用时11s,结果如下图:

